4 Ways To Better Print Security

Offices today have rules and policies about security, and some even have policies for printing. Everyone talks about policies and rules with their employees, but even the best intentions can’t always keep documents from being left behind or picked up by the wrong person. It’s up to each team member to do what is needed to keep the information confidential.
Sensitive data – like patient records, client information, or bank receipts – is easy to leave behind once printed. Think about this. What if you could add a unique digital signature that’s easy to trace to every single document? People may take better care of what they print.
There are many effective ways to set up print policies that keep documents safe. Here are some best practices that may work for you.
- Audit trails
- Encryption
- User authentication
Here are four ways to defend your network from brutal attacks.
Safeguard against breaches
Protecting information is a critical task that can damage a business if not done right. Think about how your printer down the hall; it can be overlooked, but may not be to attackers who can exploit security gaps.
Lockdown access to your network and use secure protocols to safeguard against breaches. These links can show you how to keep sensitive information from falling into the wrong hands.
Verify user identities
Knowledge is power, so knowing who uses a device is the key to print management software.
- It prevents unnecessary printing at your expense.
- It’s a safeguard to prevent unauthorized access to a print device.
Authenticate users through card swipe, ID number, password, or other methods. If you’re not using a fully authenticated network like Windows Active Directory, you may want to consider some other options to confirm identity.
Trace all print jobs
According to Quocirca,
- 11% of all security incidents are print related.
- Of those events, 59% lead to a loss of data that can cost over $380,000 each year.
Larger organizations may plan for that cost, but if you’re a small business, it could make a significant impact on your bank account.
Encourage your people to think twice about what they print, and this can be d3one by linking every document to a user. You’re likely to stop and take a second look if you know your behavior may be tracked and audited.
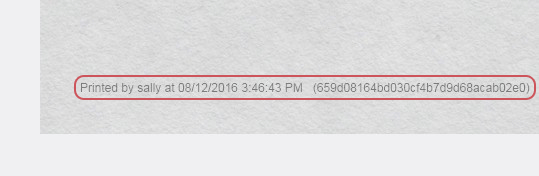
If you want to track or trace print jobs, a watermark can turn into a wealth of information in the event of a security incident. It’s an easy way to know who, what, when, where, and how a document was printed.
Meet compliance requirements
- Regular security audits ensure vulnerabilities have not crept in.
- Maintain an audit trail not only to protect your data but to protect your company.
Organizations must take ownership of how they use personal data. Keeping information secure is never easy, but it must be done. So why not use technology for document traceability and print security?
A print management solution can help put these best practices in place. Try to apply a multi-layered strategy to keep your data safe before, during, and after documents are printed.
For more information, please contact us at Stone’s Office Equipment. If you would like a free print assessment, click here.
This document was authored by PaperCut and Stone’s Office Equipment. Stone’s is an authorized dealer for PaperCut products.